Cybersecurity is not something that many companies take seriously until it is too late, says Cloudica CEO Adam Kotecki in this newest post to mark National Cybersecurity Awareness Month in October.
In his influential Sc-Fi book The Hitchhiker’s Guide to the Galaxy, Douglas Adams describes a mysterious creature that due to its lack of intelligence has a very peculiar way of defending itself.
Ravenous Bugblatter Beast of Traal (a mind-bogglingly stupid animal, it assumes
that if you can’t see it, it can’t see you—daft as a brush, but very very ravenous)
I believe that many board members in hundreds of companies behave just like the Ravenous Bugblatter – at least when it comes to devising a solid cybersecurity agenda. They close their eyes and cover their ears. They watch their pennies and are deaf to arguments. They think that somehow things will fall into place on their own.
A recent report issued by McKinsey & Company says that “few organizations have made sufficient progress in protecting information assets.”
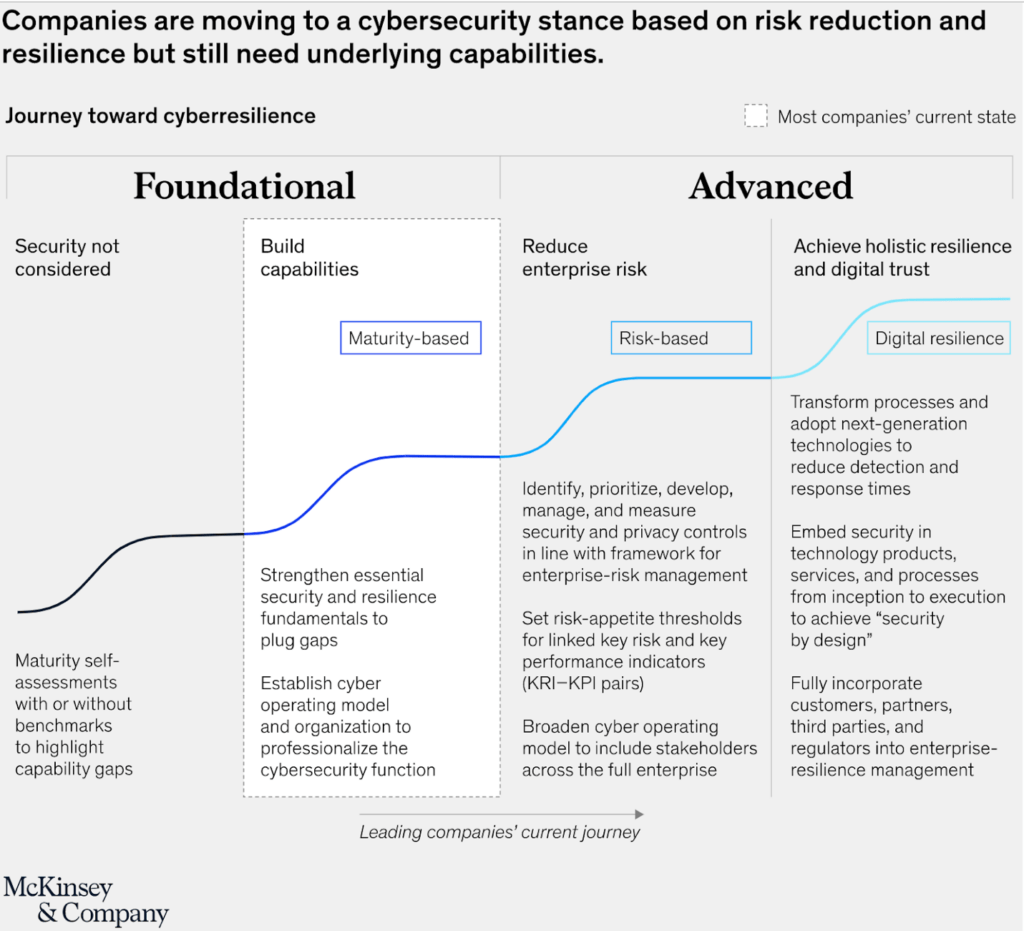
The report says that the majority of companies today are still in a “foundational” phase of developing a cybersecurity strategy for their company. However, the report adds, there is much more that needs to be done in order to achieve full digital resilience.
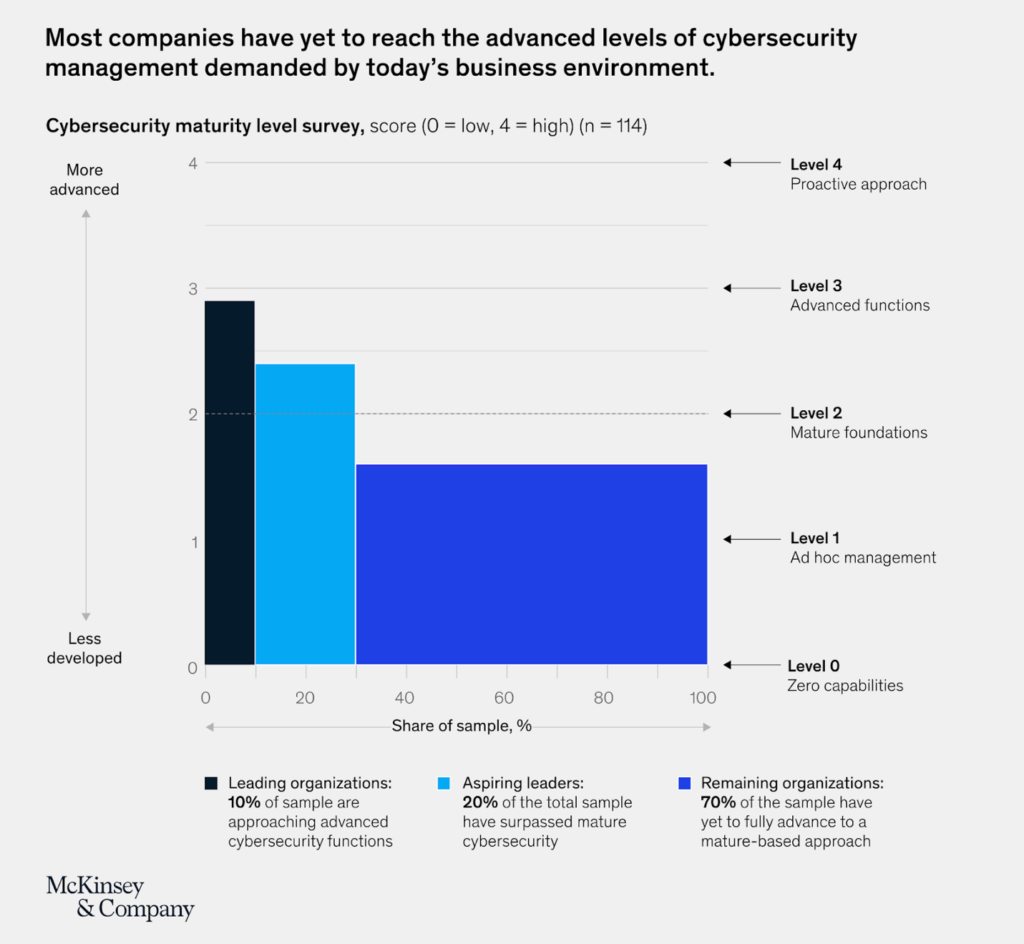
Around 70% of companies are at a stage between reactive, ad-hoc action and reaching maturity.
There probably won’t be many C-level managers who, after reading this, will conclude that they don’t want to go down this path. And yet, most companies are really only at the beginning of their journey.
What reasons do I – a cybersecurity consultant – see for such a state of affairs?
As I mentioned earlier, many companies take the “Ostrich approach” – burying their heads in the ground hoping for the worst to pass.
Another reason for this apathy is cost. When we discuss budgets or cost estimates, managers once again prefer to close their eyes and hope they will never need to go down that path.
Because at the end of the day, investing in cybersecurity is like having an insurance policy on your car. The best scenario would be to have the best-ever cybersecurity in place. And never have the need for it!
Zen and the art of risk estimation
The best argument to justify an investment in cybersecurity is to find a balance between cybersecurity costs and risks.
The simple truth is that to estimate such a balance (right in its essence) you need to understand the risk. And this is something that practically no one can realistically estimate.
In smaller and medium-sized companies, most often we often use a few formulas to come up with an answer which allows us to “have the cake and eat it too”.
Risk assessment, however, has mainly a practical purpose and is not exclusively a regulatory (ie legal) formality.
IT assessment is an activity on a “living” organism. It is like a doctor examining a patient. All sorts of things can come out, including those we would prefer to “sweep under a rug”. Often the person carrying out the audit – especially from inside the company – is in some way responsible for the results and is often on friendly terms with the very people responsible.
This is where the value of an external auditor comes in. Such an expert does not have to fear that such relationships can be damaged. He only has a desire for long-term cooperation. Employing an outside firm to examine the current state is a cost and risk.
The sad conundrum is that often only a significant failure or intrusion into important systems causes a quick wake-up call. However, I know of cases where even this is only temporary. Once sobered up, the customer forgets about the risk and even starts denying that lightning ever strikes twice. They sometimes support themselves with bad statistics and claim that the chance of another break-in is low.
My hopes in this area are raised by reports that customer awareness of these issues is rising.
Hopefully, the mentality of the Ravenous Bugblatter Beast of Traal will disappear and be replaced by factual risk analysis and a thoughtful strategy to implement cybersecurity solutions at a level appropriate to the type of company/data and risks.