The Crucial Role of Endpoint Security Policies

As business owners dive into the complex world of endpoint security, the establishment and enforcement of strong endpoint security policies appear as pivotal factors in fortifying their cyber defences. This article explores the essential role of well-crafted and enforced endpoint security policies in enhancing SMEs’ overall cybersecurity posture. The Landscape: Endpoint security involves using various […]
Effective IT Management – IT Management Challenges

Investments in IT can bring substantial benefits, but they also come with natural challenges. Recognizing and effectively managing these challenges is crucial to optimize IT infrastructure. This article explores some of the primary difficulties associated with IT management and highlights key strategies for overcoming them. Choosing the Right Solutions One of the fundamental challenges in […]
Endpoint Security: Risks and Best Practices

Endpoint devices, from laptops and smartphones to Internet of Things (IoT) devices, are gateways to an organization’s digital infrastructure. However, the convenience of these endpoints is accompanied by a variety of risks that can compromise sensitive data, disrupt operations, and expose organizations to cyber threats. In this article, we discuss the landscape of risks connected […]
What is the Cyber Resilience Act and why is it important for the EU market?

The recently proposed Cyber Resilience Act (CRA) by the European Commission is set to revolutionize the way business approaches cybersecurity. The CRA is not just another set of regulations; it’s a strategic move to enhance the security of digital products across the EU. Covering everything from baby monitors to smartwatches, this legislation demands manufacturers and […]
2024 Tech Forecast by Cloudica. Evolving Trends in IT.
As we kick off the journey into 2024, the tech landscape continues to change and bring innovations that reshape it very quickly. Join us on this adventure and let’s explore the upcoming trends and breakthroughs in IT infrastructure, Azure Cloud, M365, and IT security. 1. IT Infrastructure: Hybrid and Edge Computing Dominance In 2024, IT […]
Business potential in effective IT management

In the previous article from our “Effective IT Management” series, we identified areas where IT might need a boost. Now, let’s explore the compelling advantages that stem from investing in the right technologies and IT management practices. How IT investments support productivity, communication, cost savings and improve data security and competitiveness of the business? Let’s […]
Beyond the Breach: Healthcare data security in the face of rising cyber threats

A recent data security incident in one of the Polish medical laboratories was widely discussed among the media. The cyber attack on Alab Laboratories reminds us of the ever-growing threat cybercrime poses. Following that incident, I’d like to share my reflections and experiences on this ever-growing threat posed by cybercrime. Also, I would like […]
Microsoft Ignite 2023 – updates for security professionals

Significant enhancements to Microsoft’s suite of security solutions were announced during the latest Microsoft Ignite Conference. All designed to empower Security Operations Center (SOC) professionals in protecting assets and data more efficiently. Here’s a glimpse of the key updates: 1️⃣ Microsoft Defender XDR: Formerly known as Microsoft Defender 365, this update signifies an expansion of […]
Effective IT management

I heard this question many times: “How to improve our IT”? Managing the IT area is not only a challenge but also a key element in the functioning of any organization. Technology development, dynamic changes in the market and increasingly demanding customers make effective management of IT infrastructure and resources essential for any type of […]
Securing your cloud environment

More and more businesses are shifting to the cloud, a space full of endless possibilities and innovations. The cloud isn’t merely an option anymore; it’s a necessity for companies aiming to thrive in the digital world. It offers streamlined operations and improved teamwork but comes with a crucial condition: robust security. As businesses enter the […]
Navigating the IT Certification Maze: A CEO’s Journey and Insights

My story – Certifications in IT. Adam Kotecki, CEO Over the course of my IT career, I have earned many different certifications, each with pros and cons. In the following article, I will describe some of my experiences in earning them and their subsequent usefulness. [MCP / MCSA] In 2002, I earned my first MCP […]
Enhancing Your Cybersecurity Strength: Self-Assessing Your Company’s Cybersecurity Maturity Level

In today’s digital world, cybersecurity is crucial for the smooth operations of your organization. To effectively protect against cyber threats, it is essential to evaluate your company’s cybersecurity maturity level. This assessment will help you identify your strengths, weaknesses, and areas that require improvement. In this article, we will introduce a model for assessing cybersecurity […]
Navigating Cloud Adoption Challenges

Digital transformation has become a crucial factor in determining the success and growth of businesses, regardless of their size. For small and medium-sized enterprises (SMEs), embracing the power of the cloud can be a game-changer in achieving operational efficiency, cost-effectiveness, and staying competitive in the digital age. However, despite the numerous benefits of cloud adoption, […]
The Essential Role of People in the Generative AI Revolution

Introduction: As we navigate the transformative landscape of generative AI, one question arises: How critical are people in this revolution? It’s easy to get caught up in the excitement and potential of this groundbreaking technology, but it is crucial to recognize that people play a vital role in driving the success of generative AI implementations. […]
Creating a Cloud Disaster Recovery Plan: Ensuring Business Continuity in the Microsoft Cloud Environment

In today’s digital landscape, organizations heavily rely on cloud computing for their critical data and applications. However, the potential for unforeseen disasters or disruptions necessitates the need for a comprehensive cloud disaster recovery (DR) plan. This article will guide you through the process of creating a cloud disaster recovery plan tailored to the unique requirements […]
5 Benefits of Cloud Optimization and how to embark on an effective cloud optimization journey
Cloud optimization is crucial for maximizing the efficiency, performance, and cost-effectiveness of your cloud resources and workloads. By optimizing various aspects of your cloud infrastructure, cloud services, investments, and applications, you can achieve improved cloud performance throughout, reduced costs, enhanced security, streamlined operations, and effective cloud cost management. Let’s explore the five key benefits of […]
Hybrid Cloud Architecture: What Is It and Why You Should Care
Cloud deployment has become so confusing even smart techies like yourself can have trouble understanding it. Terms like hybrid cloud computing, clouds, multiple clouds, cloud distribution, and hyper-converged infrastructures are often used interchangeably, causing even more confusion. So, why is this concept so unclear? If you’re unsure about the hybrid cloud and how it affects […]
The Power of Physical Activity

In a world where work-life balance is increasingly challenging to achieve, Cloudica CEO Adam Kotecki shares personal reflections on the power of physical activity in enhancing his professional life.
Understanding the Importance of Multi-Cloud Architecture
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Nunc feugiat vehicula placerat. Pellentesque sit amet odio at orci aliquam convallis id vitae felis. Mauris tempor, enim vel lobortis pulvinar, augue mauris hendrerit felis.
IT’s in our DNA

Cloudica is a leading technology services provider with over 5 years of experience in providing reliable, expert technology solutions to businesses across the globe. We are dedicated to providing our clients with high-quality services that meet their needs and exceed their expectations.
A few words about valuing your work and development

You’ve probably looked at various reports or job portals more than once to see how much your position earns. Surely more than once a red light went on when you saw wide ranges and thought you were doing the same thing so maybe you should be earning more.
Permission control with Azure
AD PIM Azure AD PIM allows for effective and secure management of access to privileged roles in the Azure cloud. This solution reduces the possibility of a hacker or fraudster obtaining permissions. The functionalities of Azure AD PIM include: • “Just-in-time” access to Azure resources • Allocation of access to privileged roles within a specified […]
10 Practical Steps to Secure Your Organization from Ransomware Threats Using Microsoft Tools

Ransomware attacks have become increasingly prevalent and sophisticated in recent years, causing devastating consequences for businesses of all sizes. In this article, we will discuss ten practical steps that organizations can take to safeguard their systems and data against ransomware threats using Microsoft tools. From enabling Microsoft Defender Antivirus to implementing Azure Backup and Azure […]
The Impact of AI on IT Infrastructure and Security
As the CEO of Cloudica, a company focused on cloud technologies, I am excited to explore how artificial intelligence (AI) can revolutionize IT infrastructure and security. AI has the potential to transform the way we manage IT operations, improve efficiency, optimize performance, and enhance security measures. However, significant risk factors must also be considered. In […]
Technology Solution Advisor’s Role
Bridging the gap between technology and business: the Technology Solution Advisor’s Role In this series we would like to show you different possible career paths in Cloudica. First one is one of the key positions balancing between technical expertise of a solutions architect with the strategic insight of a business consultant, working very closely with […]
Passwordless Authentication: A More Convenient and Secure Alternative to Passwords (practical example on Azure AD)

What is Passwordless Authentication? Creating, remembering, and periodically changing passwords is no fun. Nowadays, passwords are an outdated and less secure method of authentication. Currently, a password alone is not enough security and often coexists with another authentication method. In addition to entering a password consisting of lowercase and uppercase letters, numbers, and symbols, the […]
Theory of Mind in Algorithms: Achieved!
Today, progress in technology is astonishingly fast. In my last post, I suggested that ChatGPT, especially version 4, could be perceived as a milestone, the first algorithm that we can classify as AGI, or non-narrow, specific intelligence (like a chess engine or a medical scan recognition engine), but general intelligence, “understanding” contexts, theories about theories, […]
What I talk about when I talk about… generative AI

In this blog post I’ll share some of my thoughts on the development and challenges of AI, using ChatGPT as an illustration. Through examining technological progress in recent years and its effects on our daily lives and professions, I’ve explored whether ChatGPT can be considered intelligent and what does it really mean. Additionally, I’ve addressed […]
Cloudica has been recognized in the FT 1000 ranking for 2023!

The FT1000 ranking is a list of the fastest-growing companies in Europe, compiled by the Financial Times. It identifies and celebrates Europe’s most innovative and dynamic companies, providing a snapshot of the continent’s economic growth and vitality. Joining this list for the first time is a huge accomplishment for us and an opportunity to say […]
What is digital transformation?

Digital transformation is becoming increasingly important in today’s business landscape. As the digital revolution continues to shape the way companies operate, more and more businesses are looking for ways to leverage digital information in order to maximize their competitive advantage. Defining digital transformation Digital transformation is a broad term used to refer to the transformation […]
A view from the clouds #5

Welcome to the fifth edition of News from the Clouds, the monthly newsletter from Cloudica, your trusted IT partner. An Endpoint Crystal ball Microsoft has released its latest Endpoint Management Predictions for 2023, providing insights into the latest trends and advancements in the field. These predictions are meant to help organisations stay ahead of the […]
Streamlining Operations and Boosting Productivity with Custom IT Solutions

As a business owner, you understand the importance of finding ways to increase efficiency, save time, and ultimately, boost productivity. In the past few years, technological advances have given businesses a lot of ways to streamline their operations and reach these goals. One of the most effective ways to do this is through the implementation […]
Unleash the Power of Microsoft 365: 5 Little-Known Tips for Maximum Productivity

Are you looking to boost your productivity and streamline your work processes? Look no further than Microsoft 365! This all-in-one platform is packed with features and functions, but many users don’t know about the ninja tricks that can maximize its use. In this article, we’ll reveal five little-known tips to help you get the most […]
Clear Skies Ahead: How Cloud Computing is Transforming the Digital Age

Once considered a futuristic concept, cloud computing is now an integral part of our digital lives. Over the past decade, cloud technology has revolutionized the way we store, access, and share data, making it easier than ever for businesses and individuals to maintain and utilize information quickly and efficiently. In this article, we’ll explore the […]
How to Implement a Foolproof Cybersecurity Strategy

By Krzysztof Stefański, Chief Technology Officer at Cloudica The digital age has changed the way businesses operate, offering immense potential for growth and efficiency. But this potential is also accompanied by several security risks. In order to protect their data and assets, organizations must implement a foolproof cybersecurity strategy that covers every aspect of their […]
The Benefits of Outsourcing IT Staff: How it Can Help Your Business Grow

Are you struggling to keep up with the demands of your IT department? Are you looking for ways to save costs and access specialized expertise? Outsourcing IT staff may be the solution you’ve been searching for. In this blog post, we’ll take a closer look at the benefits of outsourcing IT staff and how it […]
Why Your Company Needs a Cloud-Based Backup and Disaster Recovery Plan

In today’s fast-paced business world, data is the lifeblood of any organization. But what happens when that data is lost or corrupted due to a natural disaster, cyberattack, or human error? A robust backup and disaster recovery plan is essential to ensure that your company’s critical data is protected and can be quickly and easily […]
A view from the clouds #4

Welcome to the fourth edition of News from the Clouds, the monthly newsletter from Cloudica, your trusted IT partner. How the EU’s Data Boundary Cloud Rollout Will Shape the Future of Digital Privacy The EU Data Boundary Cloud, which went live on January 1, is a system that lets people access data stored in cloud […]
Cyberattacks on the Rise

Report shows a significant increase in volume over the past year In the past few years, cyberattacks have become more common, and both businesses and people have been hurt by different kinds of online crime. A recent report says that the number of cyberattacks around the world has gone up a lot in the past […]
How the EU’s Data Boundary Cloud Rollout Will Shape the Future of Digital Privacy
The past decade has seen an explosion in the use of cloud computing to store and manage data. However, as cloud technology has become increasingly popular, governments and organizations have been forced to grapple with the implications of storing data on cloud networks. In the European Union (EU), this has led to the development of […]
The latest trends in cloud architecture
Cloud architecture has become the go-to infrastructure for businesses of all sizes. This is because it can grow as needed, is cheap, and stores, processes, and manages data better than traditional IT systems. As cloud computing continues to evolve, the latest trends in cloud architecture are emerging. This article will talk about the latest cloud […]
What is Microsoft Azure?
Microsoft Azure is a cloud computing service created by Microsoft for building, testing, deploying, and managing applications and services through a global network of Microsoft-managed data centers. It provides software as a service (SaaS), platform as a service (PaaS), and infrastructure as a service (IaaS) and supports many different programming languages, tools, and frameworks, including […]
The road to becoming an IT professional

What are the steps to build a career in IT and how Cloudica can help you? In many lines of work – accounting, legal, management, logistics, to name a few – the school that someone graduated from is extremely important. It sets people on a solid road of development which can lead to a lifetime […]
The OECD signs “historic” privacy agreement

The agreement formally recognizes that OECD countries uphold common standards and safeguards. The Organization for Economic Cooperation and Development (OECD) has released a new international agreement that it says will assist in protecting user privacy when data is accessed for national security and law enforcement reasons. The goal of the OECD Declaration on Government Access […]
We talk to AI about cybersecurity

In recent days, ChatGPT has been making headlines. We asked it about cybersecurity and what tips and tricks it has for us to stay safe online. Below is the result. It seems that ChatGPT – an innovative Artificial Intelligence chatbot – became the first project to achieve one million users in five days. Many people […]
A view from the Clouds: #3
Welcome to the third edition of News from the Clouds, the monthly newsletter from Cloudica, your trusted IT partner. Microsoft Teams named a leading global business tool Microsoft Teams has become critical to how 270 million users around the world connect, phone, chat, collaborate, and conduct business. Microsoft has been named a Leader in the […]
Cyberattack forces French hospital to suspend operations

Local news reports say that a hospital in the Paris suburb of Versailles was shut down over the weekend. This meant that all surgeries had to be postponed and some patients had to move. According to Franceinfo, a cyberattack hit the André-Mignot hospital in Chesnay-Rocquencourt, Yvelines, around 9 p.m. local time on Saturday evening, rendering […]
Microsoft named leader in Gartner Quadrant for Teams messenger solutions
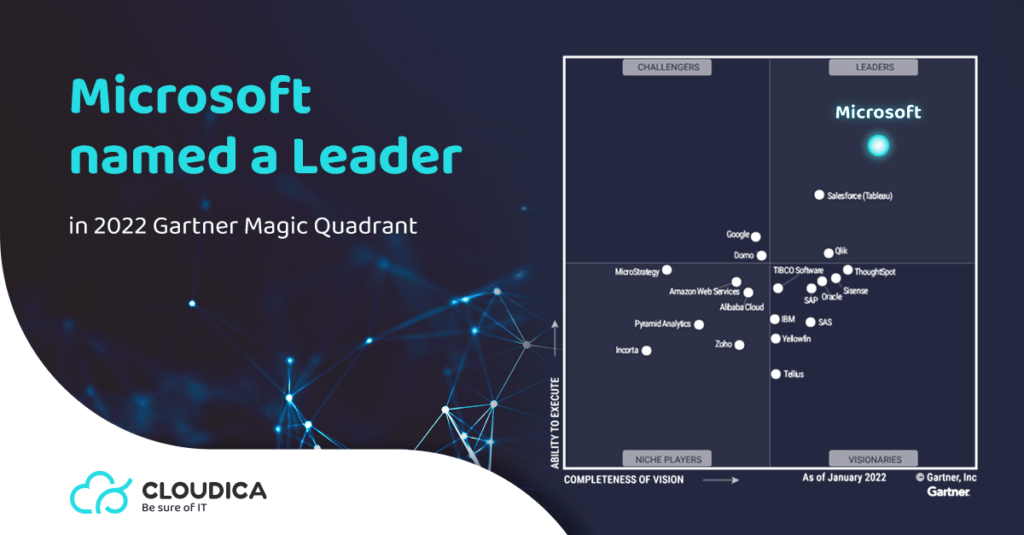
Microsoft Teams has become critical to how 270 million users around the world connect, phone, chat, collaborate, and conduct business. As the world recovers from the pandemic, Microsoft Teams is witnessing higher use and engagement – on average, users connect with Teams 1,500 times per month and spend more time in Teams chat than they […]
Black Friday is a hacker’s holiday, says think tank

Black Friday shoppers should be on the lookout for new scams launched by hackers in the days leading up to the event. With hackers impersonating well-known businesses, Check Point Research (CPR) said that the team has already noticed a dramatic rise in phishing attempts involving online shopping. According to a recent CPR statement, “While consumers […]
A Cloud for 8 billion

As the global population hits eight billion today, we are faced with a profoundly serious question: how to deal with a rapidly growing global community, and can cloud technology offer a solution? Adam Kotecki is the CEO of Cloudica, a cloud-solutions provider and consultancy firm based in the EU. “Rapid population growth is at the […]
Global cyberattacks are growing at a fast pace: Microsoft report

Microsoft has issued its annual Digital Defense Report, which detailed the cyber threat landscape and digital defense tactics implemented and discovered by the company between July 2021 and June 2022. According to the research, nation-state cyberattacks on key infrastructure have surged by 20 to 40% in the last year. The Seattle-based company blames the increase […]
A view from the Clouds: #3

Welcome to the third edition of News from the Clouds, the monthly newsletter from Cloudica, your trusted IT partner. Microsoft Teams named a leading global business tool Microsoft Teams has become critical to how 270 million users around the world connect, phone, chat, collaborate, and conduct business. Microsoft has been named a Leader in the […]
US Federal agencies issue guide on how to deal with DDoS attacks

The Federal Bureau of Investigation (FBI), the Cybersecurity and Infrastructure Security Agency (CISA), and the Multi-State Information Sharing and Analysis Center (MS-ISAC) have issued collaborative instructions for reacting to distributed denial-of-service (DDoS) assaults. “Organizations should include steps to address these potential effects in their incident response and continuity of operations playbooks,” the three agencies wrote […]
Prevention is better than cure: the most common reasons for implementing cybersecurity solutions
Cybersecurity is not something that many companies take seriously until it is too late, says Cloudica CEO Adam Kotecki in this newest post to mark National Cybersecurity Awareness Month in October. In his influential Sc-Fi book The Hitchhiker’s Guide to the Galaxy, Douglas Adams describes a mysterious creature that due to its lack of intelligence […]
Cybersecurity at the fore

Cloudica looks at some of the finer points of online safety this October during National Cybersecurity Awareness Month. To mark this occasion, we would like to draw the spotlight on this topic which is very close to our hearts. 95% 68 percent 1,862 of cybersecurity breaches are caused by human error of business leaders feel […]
Recruitment in tech: What do IT professionals look for when considering a career change?

While in the past, salaries were the dominant factor, nowadays, people are also looking at other points in recruitment advertisements, says Przemysław Dudek, Chief Financial Officer at Cloudica. Which factors do IT professionals look at before applying for a job in the sector? This is a hard question, and I will answer like an engineer: […]
Apple solutions receive security clearance from German authorities
![[13:46] Roberto Galea iOS solutions are 'secure' says Germany's BSI](https://cloudicagroup.com/wordpress/wp-content/uploads/2022/10/MicrosoftTeams-image-36-1024x535.png)
The German Federal Office for Information Security (BSI) has evaluated Apple’s solutions and issued a security clearance allowing iPhone and iPad devices to process information classified as “official”. This applies to native, built-in mail, calendar, and contacts applications, without the need for paid add-ons, extensions, or third-party applications. BSI has examined the general security properties […]
Cloudica aims to leave no one behind

Cloudica CEO Adam Kotecki recently gained a new certificate. In this blog post, he talks about why inclusive leadership is important within Cloudica and how he plans to involve it more in the business moving forward. Creating diverse workplaces – where each person is valued, heard, and given the opportunity to advance as far as […]
Back to Basics: Azure Kubernetes Service
We cannot stop the inevitable growth of applications across multiple servers. But there is a way to manage the data in a better way. Data can be processed even more efficiently and in a scalable way in containers managed by Kubernetes offering an open-source API that regulates how and where those containers will execute in […]
Core Values: Expertise

Welcome to the last of four articles based on our Core values introduced as part of Cloudica’s rebranding to mark five years of business. The first letter of each of the four Core values marks a letter in the word Core: Conscientiousness, Openness, Reliability, and Expertise. Today we’ll focus on the fourth value. In order […]
A View From the Clouds

A monthly newsletter from Cloudica, your trusted IT partner. Welcome to the first issue of “A View From the Clouds”, our monthly newsletter where we will be bringing you up to speed with what is happening in our company and beyond. First, let’s kick off with a generous thanks to all the people involved in […]
Core Values: Reliability

Welcome to the third of four articles based on our Core values introduced as part of Cloudica’s rebranding to mark five years of business. The first letter of each of the four Core values marks a letter in the word Core: Conscientiousness, Openness, Reliability and Expertise. Today we’ll focus on the third value. The cybersecurity […]
Core Values: Openness
Welcome to the second of four articles based on our Core values introduced as part of Cloudica’s rebranding to mark five years of business. The first letter of each of the four Core values marks a letter in the word Core: Conscientiousness, Openness, Reliability, and Expertise. Today we’ll focus on the second value. When the […]
Partner Update: Fortinet named Leader in Gartner Quadrant

Cloudica partner Fortinet has been named a “Leader” in the latest software-defined wide area network (SD-WAN) Quadrant by Gartner. This is the third year in a row that Fortinet has received such a prestigious mention. Fortinet also placed highest in Ability to Execute in both 2021 and 2022. Cloudica CEO Adam Kotecki said that he […]
IT professionals today: how the IT job market has evolved in recent years

By Adam Kotecki, CEO of Cloudica The IT sector is one of the swiftest growing industries worldwide, as more and more professionals join this exciting and fast-paced environment. But the general profile of the typical “IT professional” is also enjoying a renaissance. “Hello, IT. Have you tried turning it off and on again?” is the […]
Core Values: Conscientiousness
Welcome to the first of four articles based on our Core values introduced as part of Cloudica’s rebranding to mark five years of business. The first letter of each of the four Core values marks a letter in the word Core: Conscientiousness, Openness, Reliability, and Expertise. Today we’ll focus on the first value. Over the […]
Welcome to the next chapter in Cloudica’s story

It was exactly five years ago when Adam, Krzysztof, and Przemek decided that the time was right to take on the world with their own company. By then, all three already had around 15 years of experience in the IT industry, and while they realized that the road ahead was going to be tough, they […]
The problem with the ‘Schrödinger backup’

Cloudica CEO Adam Kotecki puts on his scientist hat to look at one of the problems faced by data security professionals today: “is my data safe or not?” Today’s publication will be a bit unusual. There will be both a little (quantum!) physics and a little computer science. This article will teach you: who Erwin […]
Reach for the sky: Cloud Solutions for your business

Reaching New Heights: Elevating Your Business with Cloud Solutions In today’s rapidly evolving business landscape, having a website and email alone is no longer sufficient. To stay competitive, businesses of all sizes, from local corner stores to Fortune 500 companies, are recognizing the need to expand their operations online. Cloud solutions provide a transformative approach […]
Five tips to keep your company safe online

Five tips to keep your company safe online With cyberthreats becoming an ever more common problem, let’s look at a number of ways you can keep your company data safe online. The internet is a vast space and while it can be indispensable for companies to rely on cloud computing for many aspects of their […]



